
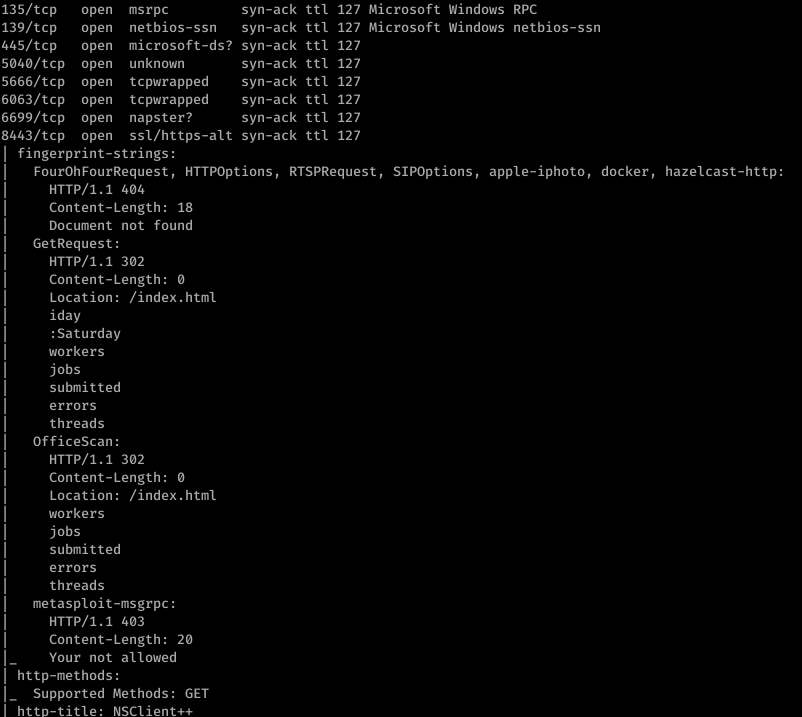
So I fired off AutoRecon (written by Tib3rius) and after it was done, this is what nmap found:

Alright, well let’s start with ftp. After getting anonymous access to ftp, I found this:
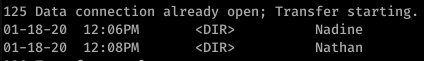
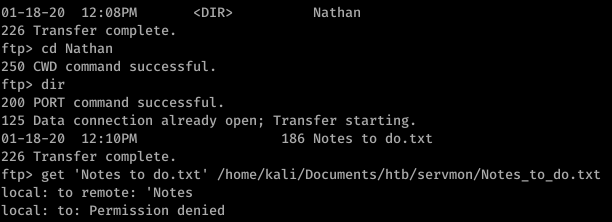
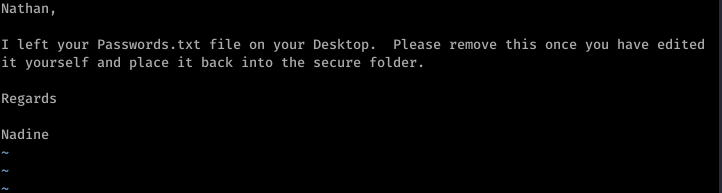
So that’s a hint that Passwords.txt is a file under Nathan’s username. Using basic knowledge of Windows file system mapping, we can guess at where exactly this file is. Something like C:\Users\Nathan\Desktop\Passwords.txt maybe?
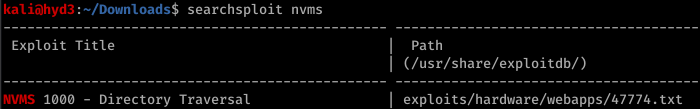
Enumerating further, we find that Port 80 runs something called NVMS. Let’s look on Searchsploit for nvms:
Before we go to trying to exploit this… let’s continue properly enumerating. Port 8443 has something called NSClient++ running on it.
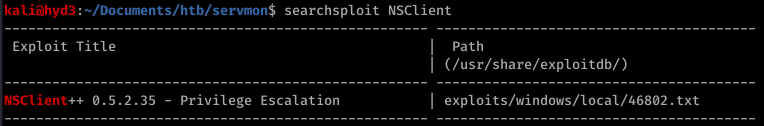
Okay so we have a priv esc possibility in our back pocket.
Firing off burp, we use the directory traversal to see if anything good comes of that guess on Passwords.txt’s location

Sweet. Now doing a bit of research, we can also find the location of the file that contains the password for NSClient++. It’s in a file called nsclient.ini. Reading this file, we get another password

However, it looks like we can only log into this from the “allowed host” of 127.0.0.1.
Trying to use the list of passwords found in Passwords.txt with nadine and SSH, we eventually get in with username: nadine and password: L1k3B1gBut7s@W0rk

Now that we’re in, let’s focus on our initial hunch of using NSClient++ to priv esc. First, we use plink.exe to set up a port forward via SSH

Now this took a bit of messing around with, but eventually what I did was uploaded nc.exe into temp and created a bat file to return a reverse shell.

The WebUI was pretty difficult to understand how to work so I ended up reading documentation and using the API to put the script rev.bat onto the box

To trigger the script, I then booted up the WebUI and ran scripts\ex\rev.bat in the console

On our listener, we get an NT AUTHORITY\SYSTEM shell














