
Let’s start off with our portscan:

Looks like only port 80 is open. Running gobuster on port 80, we get some interesting directories:

After going down the list, we see /dev’s contents:
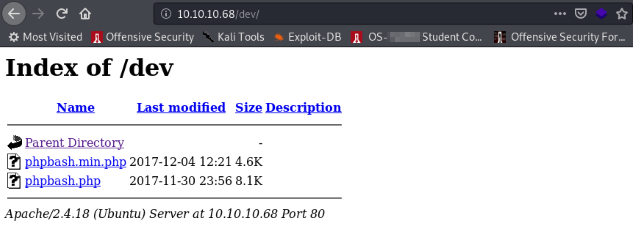
What’s phpbash.php ?

It’s an interactive web shell. Well that’s pretty straight forward. Using this payload from the pentestmonkey website:

We get a reverse shell on our listener:

Grabbing the user.txt flag:

So let’s look around and MANUALLY enumerate before we try to use scripts. Manual enumeration is always preferred because you’re being more intentional on what you’re looking at. And to be honest, scripts can always miss stuff.
Running PS -ef we see that there is a cron job running every minute:

So let’s try to read test.py

Womp womp. Okay… well let’s try to do something that we should have done right away in the first place: sudo -l

So this is interesting. We know that scriptmanager is a user on the box. This took me a little bit, but I eventually got it (of course, syntax error):

So now, I can read test.py. Now that I am scriptmanager, I’m willing to bet that test.py is executed by root. I just need to create my own test.py and replace what’s in there.

Once I put this on the box, I tested it first to make sure it worked … of course I had a few issues prior to getting the script right but that’s why we test first!


Ok so the script works. Time to let the cron run and start our listener and wait patiently for root to execute the script:
